Analyzing Encrypted Traffic with Wirehark¶
To present a detailed, protocol-aware view of network packets, Wireshark uses a library of decoders to parse and interpret the headers and data at each layer of the network protocol stack. With support for thousands of protocols, Wireshark is even able to provide a rich view of application layer messages.
By default, strong encryption limits Wireshark's feature set. As a passive observer of conversations, Wireshark is not able to obtain or compute encryption keys that are needed to decrypt network traffic that it observes. To work around this limitation, Wireshark can be configured to load the TLS session secrets from a filesystem based log. Wireshark uses these secrets to generate handshake and application traffic keys that allow it to fully decode each step of the TLS handshake and higher-layer application traffic.
Logging Keys from TLSContext¶
The TLSContext class that is defined in the project repository includes a log_keys() method that generates the log entries needed to facilitate this process. This method emits four rows of text representing the client/server handshake secrets and the client/server application secrets. Each of log entry is also associated with the client random value from the current session's Client Hello. This value enables Wireshark to quickly identify a TLS session and select the appropriate secrets from the log file.
To save these entries into a Wireshark-compatible log file, update your handshake code to append the new secrets to a file. The following example creates or updates a file named info314_tls13_keys in the current user's home directory.
home_directory = os.environ['HOME']
with open(f'{home_directory}/info314_tls13_keys', 'a') as f:
entry = context.log_keys()
f.write(entry)
- Call
tls.generate_handshake_keys()andtls.generate_application_keys()beforelog_keys()method. For a more flexible approach, please follow the steps in Updated Key Logging Methods.
Wireshark TLS Preferences¶
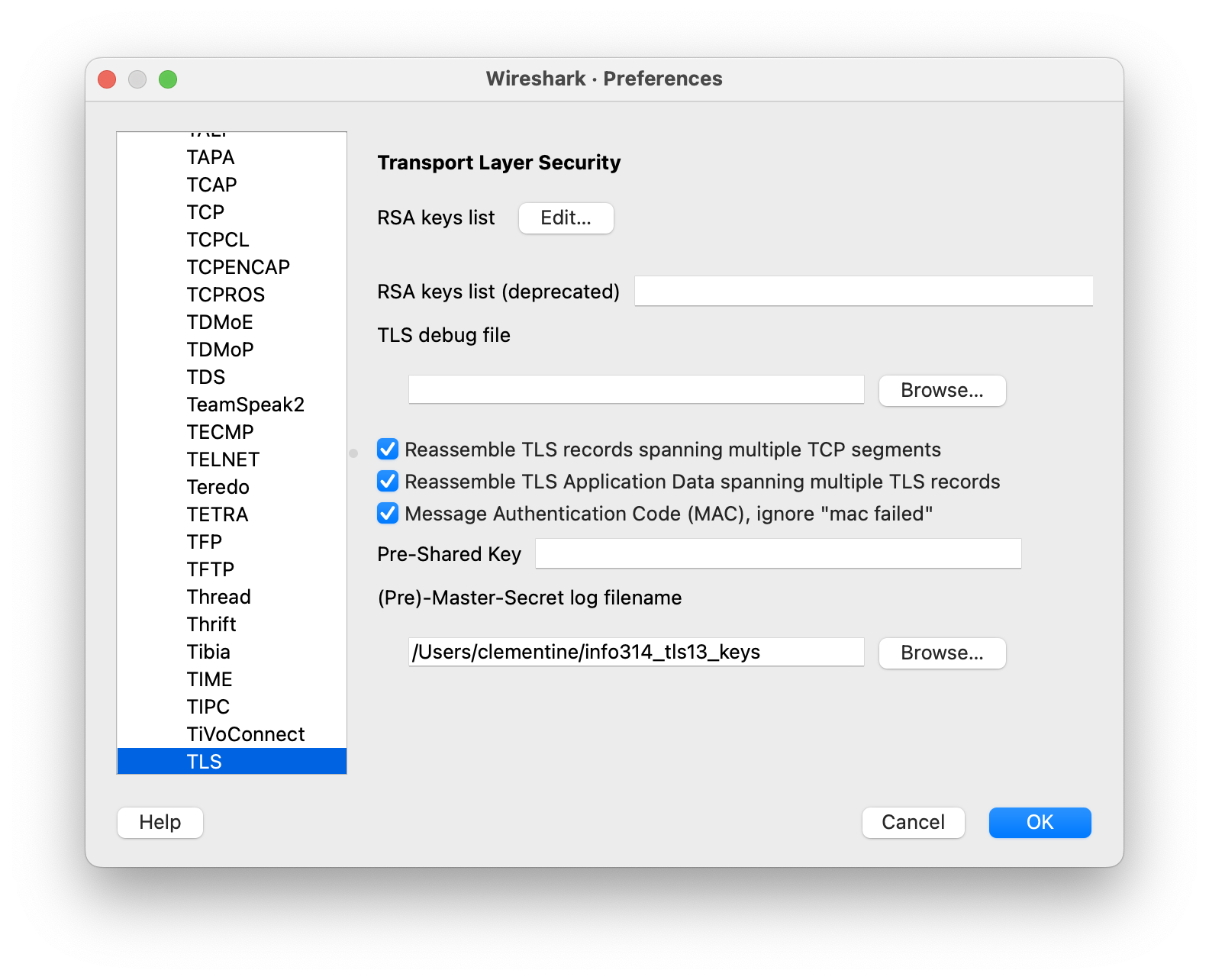
To start analyzing encrypted traffic, add the location of the log file to TLS protocol preferences in Wireshark:
- Open Wireshark's preferences pane
- Expand Protocols in the left pane of the preference window and scroll until you find TLS.
- Enter the full path to the log in the (Pre)-Master-Secret log filename.
- (Optional) Select or deselect from the default options to control Wireshark decoding behavior:
- Reassemble TLS records spanning multiple TCP segments
- Reassemble TLS Application Data spanning multiple TLS records
- Message Authentication Code (MAC), ignore "mac failed" (useful for debugging)
Updated Key Logging Methods¶
For more flexibility, update helpers.py and add the following snippet immediately before or after the existing log_keys() definition. These methods will emit handshake and application keys in separate steps, which makes it somewhat easier to troubleshoot issues associated with the completion of the handshake.
def log_handshake_keys(self):
out = f"CLIENT_HANDSHAKE_TRAFFIC_SECRET {self.client_random.hex()} {self.client_handshake_secret.hex()}\n"
out += f"SERVER_HANDSHAKE_TRAFFIC_SECRET {self.client_random.hex()} {self.server_handshake_secret.hex()}\n"
return out
def log_application_keys(self):
out = f"CLIENT_TRAFFIC_SECRET_0 {self.client_random.hex()} {self.client_application_secret.hex()}\n"
out += f"SERVER_TRAFFIC_SECRET_0 {self.client_random.hex()} {self.server_application_secret.hex()}\n"
return out