Lab 4 - Analyze TCP with ncat and Wireshark¶
Lab 4 Assignment page on Canvas
Overview¶
The purpose of this lab is for students to gain hands on experience with TCP connections. By the end of the lab you will be familiar with:
ncat- TCP handshakes
- http
- https
- Security faults of http
We highly recommend using search engines to help you find solutions.
Setup¶
For this lab, we are going to use the incredibly versatile ncat utility to directly read and write data to and from HTTP(s) servers.
Some of you may already be familiar with a similar tool known as netcat (nc from the command line on most Linux or macOS machines). ncat is a re-implementation of netcat that adds some handy features (like SSL/TLS connections).
Installing ncat¶
Please follow instructions to install ncat from https://nmap.org/ncat/. You can accomplish this either by installing the nmap port scanner suite or by installing the portable executable.
Please test your installation by running ncat from a new Powershell console.
You may need to update your system path to include the directory in which you installed ncat.
Install nmap from your preferred package manager (e.g., apt or brew) or follow instructions provided at nmap.org.
Part I - TCP Analysis Introduction¶
Capture¶
The instructions below can be used to manually perform an HTTP exchange with a server via the ncat tool. This process approximates the exchange that occurs between your web browser and a web server after you enter a URL into the address bar or click on a hyperlink.
Why don't I see any output?
At this point, we're interacting directly with a server in a text-based protocol. The server will wait silently for you to enter a valid message. Per RFC 2616, the request you are sending is multiple lines and is terminated by two new lines.
If you wait too long or submit something that violates the specification, the server will respond with an error and close the connection.
Capture Instructions¶
-
Create a capture filter that will select traffic appearing on TCP port 80 or 443.
-
Launch a new Wireshark capture on your primary network interface with the capture filter from Step 1.
-
Launch a couple of new terminals (mac/linux) or Powershell consoles (windows) and follow these steps to make HTTP requests to neverssl.com and wikipedia.org (in separate consoles):
- NeverSSL
- a. Open a new connection:
ncat neverssl.com 80
- b. Start a new HTTP requests (terminated with a newline)
GET / HTTP/1.1
- c. Add a Host header followed by two new lines
Host: neverssl.com
- a. Open a new connection:
- Wikipedia
- a. Open a new connection:
ncat --ssl www.wikipedia.org 443
- b. Start a new HTTP requests (terminated with a newline)
GET / HTTP/1.1
- c. Add a Host header followed by two new lines
Host: www.wikipedia.org
- a. Open a new connection:
- NeverSSL
-
Close your connections with CTRL-C
-
End your Wireshark capture and save a copy of the capture to complete the remaining analysis.
-
Save the
ncatoutput to a notepad or file (for questions 3 & 4 on the lab report).
Report¶
-
What capture filter did you use to select TCP traffic on ports 80 and 443?
-
Briefly describe the difference between a capture filter and a display filter. In what way do they serve different purposes?
-
Paste in the first 10 lines of Wikipedia's server's response from the
ncatoutput. -
Paste in the first 10 lines of NeverSSL's server's response from the
ncatoutput.
Part II - Plaintext (http) Analysis - NeverSSL¶
Perform a search in Wireshark (CMD-F or CTRL-F) to find the string neverssl.com in packet details.
Note
You'll need to adjust the options for your search via dropdowns
This search should lead you to the reassembled HTTP session. Review the summary of the reassembled TCP segments provided inside the Packet Details. For an alternate perspective, right click on any frame belonging to the connection and select Follow -> TCP Stream. Finally, right click on any frame in the connection and select Prepare Conversation Filter -> TCP
Report¶
-
Fill out the table in the lab report template for the first 10 frames of the NeverSSL connection in Wireshark by identifying each frame's:
- Frame #
- Source (client or server)
- Flags
- Sequence number
- Acknowledgement number
- Length of payload (additional data)
(If you are confused about table syntax in Markdown, go here and scroll to to "Tables")
-
Which information is used by the client to identify messages from the connection?
-
Which information is used by the server to identify messages from the connection?
-
Fill out the table in the lab report template for the last 5 frames of the NeverSSL connection in Wireshark
Part III - Encrypted (https) Analysis - Wikipedia¶
Perform a new search in Wireshark to find wikipedia.org. Be careful with this search since the search term appears in the page content from neverssl.com. Once you have identified the a frame from this TCP connection, prepare a new conversation filter so that you can take a closer look at the session.
Hint
We are looking for the term to appear in a Transport Layer Security option. We won't actually see the contents of our HTTPS session since the connection is encrypted by the time we enter it.
Note
It may be helpful to create a table or illustration that lists significant frames and their role in the session.
Report¶
-
Fill out the table in the lab report template for the first 10 frames of the Wikipedia connection in Wireshark
-
Fill out the table in the lab report template for the last 5 frames of the Wikipedia connection in Wireshark
-
What is the frame number of the first frame to contain a Transport Layer Security header?
-
Looking at the first frames of the SSL/TLS session, identify the messages sent in the TLS handshake (hint: look for Handshake Type in the packet details).
-
Create a display filter to show the server side of the conversation only.
-
Can you find any stream anomalies, e.g., duplicate data, out-of-order segments, or duplicate ACK numbers? (Hint: These are labeled in the Info field of the packet list)
Part IV - General TCP Analysis¶
Report¶
-
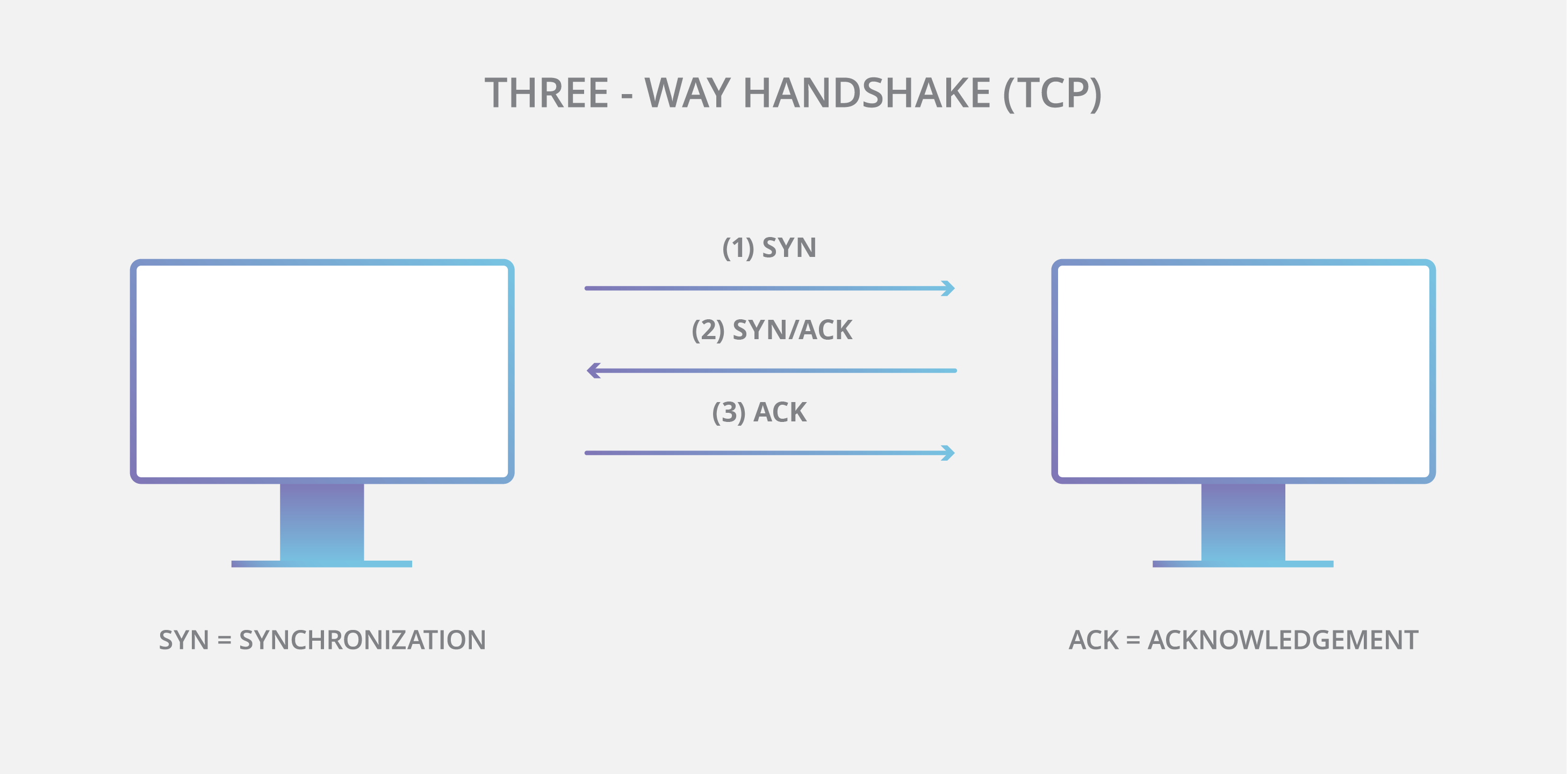
What function does the opening handshake of TCP accomplish?
-
Describe how you would identify stream anomalies by using sequence and acknowledgement numbers of TCP segments.
Bonus (Optional)¶
Report¶
- (5 points) Create a basic sequence diagram of the TCP segments sent in wikipedia.org session.
Do not diagram all 100+
Do not diagram all 100+ frames of the wikipedia.org session, but you should include enough to illustrate the TLS handshake, the first few frames of encrypted data, and the closing of the TCP socket.
You can draw this out on paper and submit a scan or use any other tool capable of building diagrams. Take a look at https://websequencediagrams.com.
Your diagram should include annotations for the following details:
- Frame # (on each message)
- TCP Flags (on the setup/teardown handshake)
- TLS Handshake Protocol steps (if applicable)
- # of bytes transferred (messages carrying data)
Hint: Be careful to exclude reassembled messages from your diagram (e.g., frames labeled HTTP or TLS that represent multiple TCP segments).